to the next level?
Your Business,
Our Platform
Elevate your distribution, manufacturing, and warehousing operations with Iptor Unified Platform – the intelligent ERP solution that adapts to your unique needs
What is Iptor Unified Platform?
Iptor Unified Platform empowers distribution, warehousing, and manufacturing businesses with a robust ERP solution. Built upon the proven DC1 ERP engine, it delivers a modern user experience, flexible deployment choices (cloud or on-premise), and a thriving ecosystem of integrations. This powerful combination streamlines operations, boosts efficiency, and drives significant business growth.
Our Mission is to provide businesses with a unified ERP solution that delivers measurable value by driving growth, enhancing efficiency, and enabling them to adapt to the evolving needs of their customers and the market. Our Vision is to lead the evolution of ERP for distribution, warehousing, and manufacturing industries, delivering innovative solutions that drive operational excellence and empower businesses to thrive in the digital age.
FOR A DIGITALLY POWERED DISTRIBUTION INDUSTRY:
SMART FUNCTIONALITIES AND FLEXIBLE DEPLOYMENT
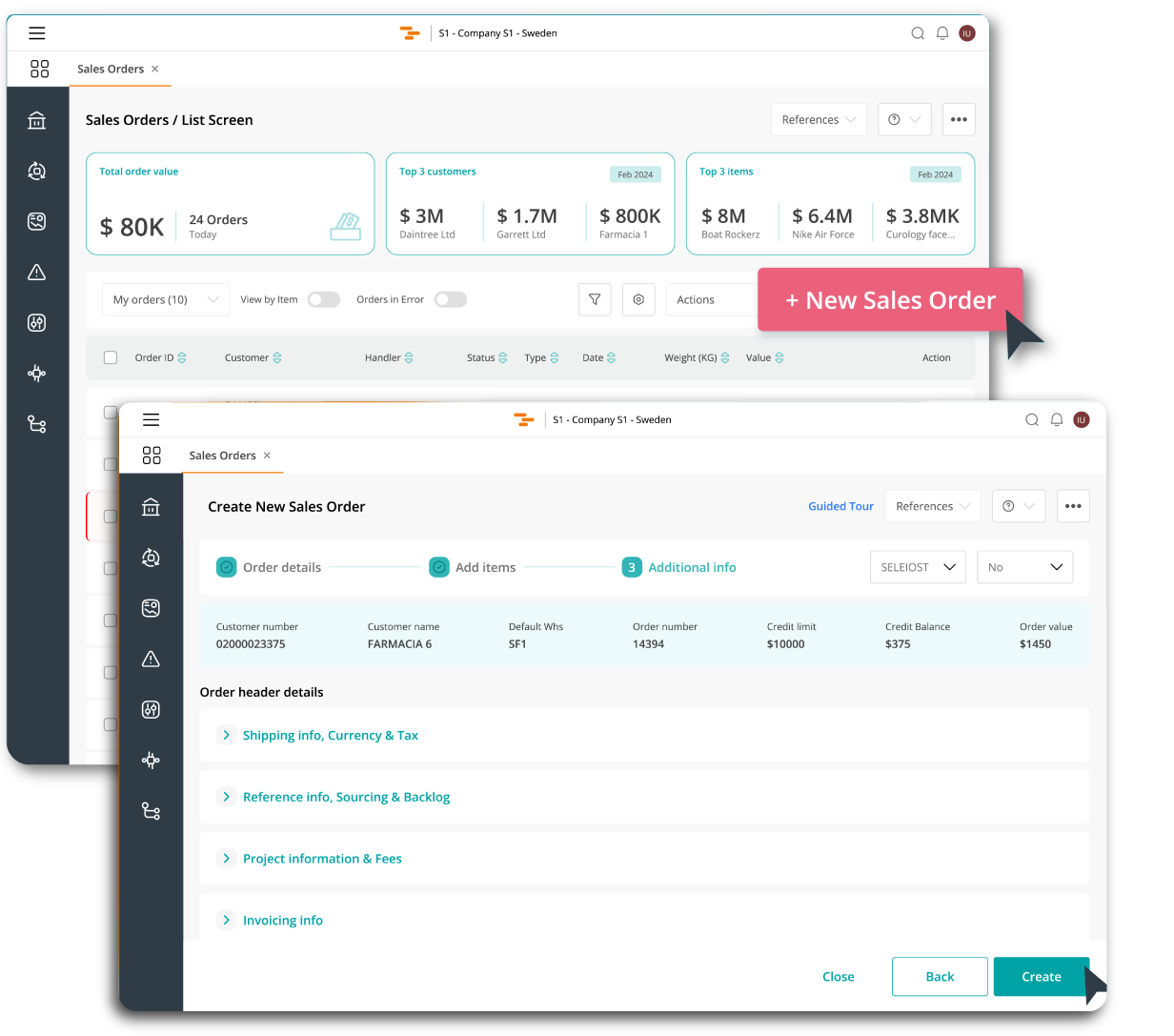
-
Streamlined Operations
AI-powered automation and real-time insights drive intelligent process automation, boosting productivity and reducing errors
-
Flexible Deployment
Businesses gain flexibility by choosing from cloud, on-premise, or hybrid deployments, enabling seamless transitions between options -
Enhanced User Experience
Customizable dashboards and mobile accessibility, combined with an intuitive interface, enhance user adoption and satisfaction -
Scalable Growth
A modular architecture, combined with preconfigured processes and global regulatory management, enables businesses to adapt quickly to market changes -
Robust Security and Compliance
24/7 surveillance, audit trails, and secure permissions ensure data protection and compliance with industry standards -
Seamless Integration
Extensive API support and a platform for custom integrations enable seamless connectivity across the business
WHAT’S YOUR BUSINESS SECTOR?
BENEFIT FROM OUR INDUSTRY PROVEN SOLUTIONS

IPTOR UNIFIED PLATFORM
Distribution
Optimize your supply chain, enhance inventory management, and improve customer satisfaction with our tailored distribution solutions

IPTOR UNIFIED PLATFORM
Manufacturing
Streamline production processes, reduce waste, and increase operational efficiency with our comprehensive manufacturing ERP tools

IPTOR UNIFIED PLATFORM
Warehousing
Maximize space utilization, improve order accuracy, and accelerate fulfillment with our advanced warehousing management features
A SOLUTION TO CONQUER EVEN THE MOST COMPLEX FULFILLMENTS CHALLENGES
Iptor Unified Platform is developed for the toughest challenges in distribution. A solid and industry proven software solution that grows with your business needs. That is what we offer.
Frequently asked questions
How long does it take to implement Iptor Unified Platform?
Implementation time varies based on your specific needs, but our streamlined process and expert support team ensure a smooth and efficient deployment.
Can Iptor Unified Platform integrate with my existing systems?
Yes, our extensive API support and partner ecosystem allow for seamless integration with a wide range of third-party applications and legacy systems.
How does Iptor Unified Platform ensure data security?
We employ state-of-the-art cybersecurity measures, including encryption, regular security audits, and compliance with industry standards to protect your data.
What kind of support is available after implementation?
We offer comprehensive post-implementation support, including 24/7 technical assistance, regular updates, and access to our community forum and knowledge base.
Can Iptor Unified Platform scale as my business grows?
Absolutely. Our modular architecture and flexible deployment options ensure that the platform can easily adapt to your changing business needs.
Speak to an Expert!
We understand our role as a trusted advisor and are here to support you. Would you like to receive more information about Iptor Unified Platform or a special industry solution without obligation? Or would you like to make an appointment with our service team? We put our know-how at your disposal.




Peer to peer with the leaders in pharma industry Iptor developed a highly efficient and well proven pharmaceutical distribution software. Download our whitepaper to better understand what small and medium-sized pharma distributors and manufactures must consider to meet the requirements of DSCSA.
YOU’RE IN GOOD COMPANY
Over +4,300 instalations so far


